M02 Ethernet, Switching and VLANs
Lecture Videos
Ethernet
Background
Ethernet is the dominant network connectivity protocol on the OSI Model Layers 1 & 2. Most of common users have heard of it, sometimes it is used to refer to a certain cable, and so on.
Ethernet makes it plausible to connect devices through different physical topologies. The word topology is often used, but in this case we mean the physical characteristics of connections.
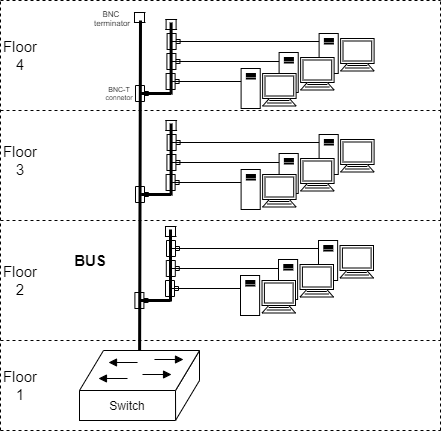
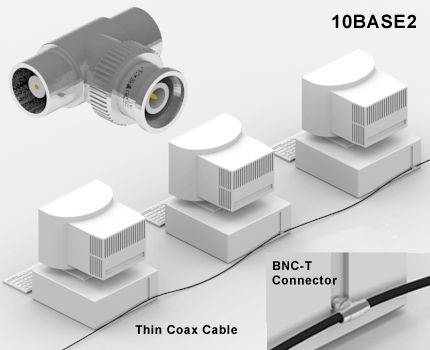
Topologies of a Network: BUS
BUS -topology is one of the oldest topologies. A singular coaxial cable that connected all the machines through T-junctures. Sometimes referred as "Thin (or) Thick Ethernet" based on the cabling ... thickness.
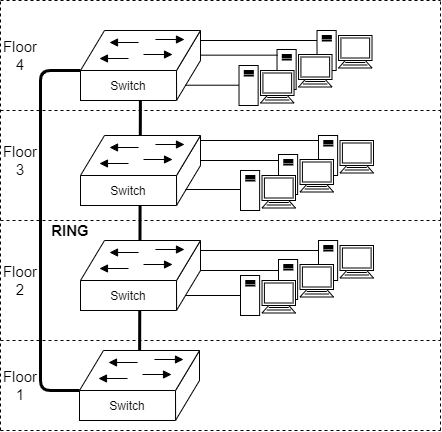
Topologies of a Network: RING
A more modern solution. Notice that ring allows the traffic to have east and west exits in case of a link failure between devices. Most commonly used in WAN networks today.
Topologies of a Network: STAR
Star is the basic connectivity of end points to a network. No matter the technology, one device acts as a connecting device to as many end devices as possible. The device is a single point of failure for those end devices.
This topology is often used when a singular switch servces 24 to 48 different ethernet connections (based on how many ports it has).
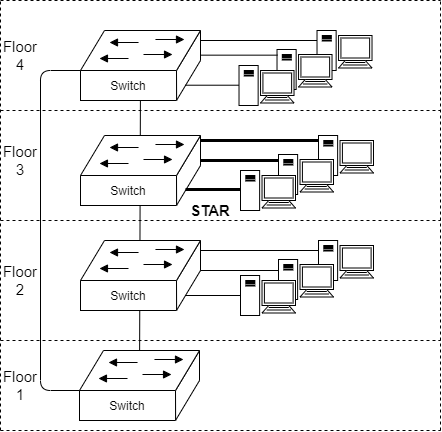
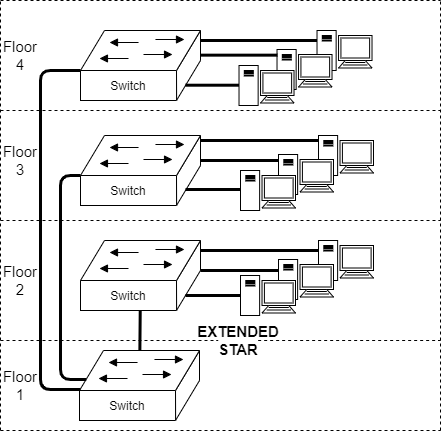
Topologies of a Network: EXTENDED STAR
The star topology can continue up the topology tree. Notice how the switches are connected as a star to the one in the basement. Sometimes this is also called a Tree topology. It is a alternative to Ring topology, but typically avoided if possible.
The switch in floor 1 acts as a single point of failure for the whole building.
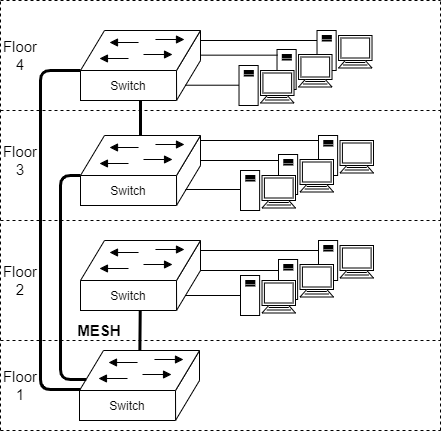
Topologies of a Network: MESH
Mesh topology is usually a unorganized attempt to provide redudancy to the network. Normally a ring topology would suffice, but just to be sure... additional links have been added. It makes sense, but causes (sometimes) illogicality and chaos when troubleshooting a network.
This doesn't mean that mesh topology doesn't have its situations.
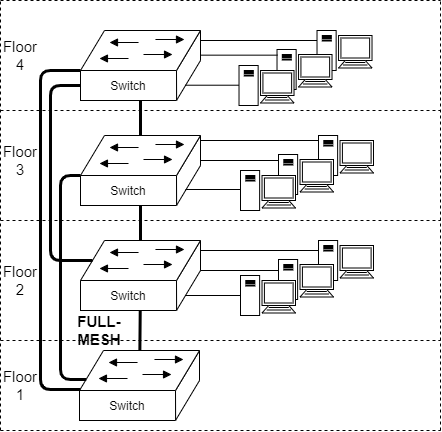
Topologies of a Network: FULL MESH
Full-mesh is the ideal solution for all networking. If we would live in an utopia, this would be the way how all networks should be formed. All the nodes have links to all other nodes... creating a full-mesh. However as we have to abide to the laws of physics; this isn't feasible/possible/affordable solution.
Full-mesh equation is something to remember for network engineers
n*(n-1)/2, where n is the amount of network devices
Examples
5*(5-1)/2 = 10 links
7*(7-1)/2 = 21 links
14*(14-1)/2 = 91 links
49*(49-1)/2 = 1 176 links
When ever an engineer sees an full-mesh requirement, it normally means problems in scaling the solution.
Speeds
Below is the rough timeline of the speeds of Ethernet. Standards have been in development earlier, but actual release and spread to industry (and hardware) a little bit later.
| Timeline | Speed |
|---|---|
| ~1972 | 2,94 Mb/s |
| ~1980 - 1985 | 10 Mb/s |
| ~1995 | 100 Mb/s |
| ~1998 | 1000 Mb/s (or 1 Gb/s) |
| ~2010 | 10 Gb/s |
| ~2014 | 40 Gb/s |
| ~2018 | 100 Gb/s |
| (~2016) | (2.5 Gb/s) |
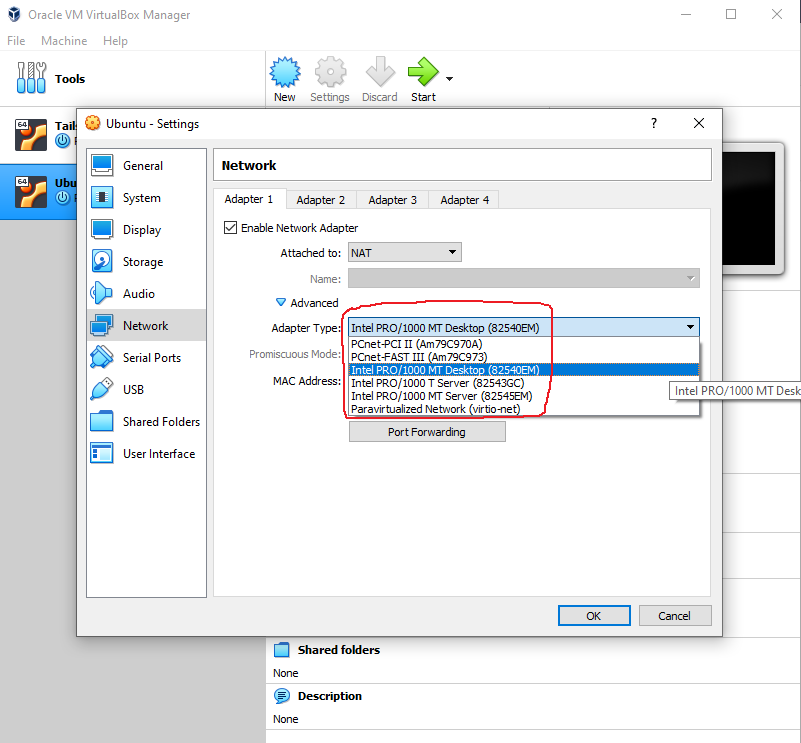
Warning: When configuring a virtual machine, the Adapter Type of the virtual machine also sets its Ethernet speed
The naming of the adapters is rather ... varying in VirtualBox
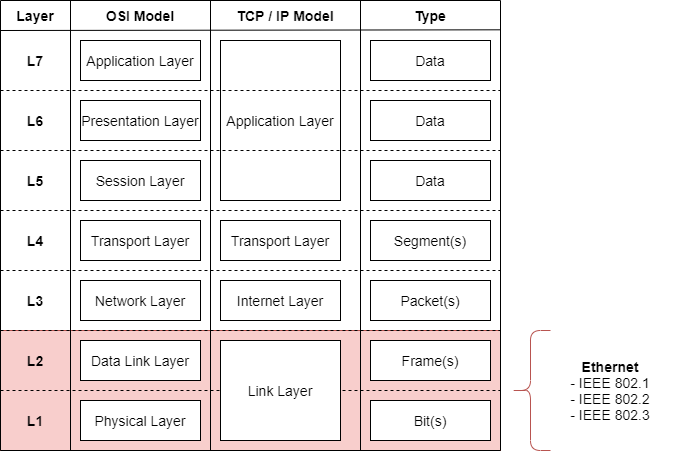
Ethernet is an Layer 1 & Layer 2 protocol of the OSI -model. The standards take into account the physical connection and modulations used within the wires.
Media Access Control - MAC
Video: Data Networks, Ethernet, Switching and VLANs, part 2
Addressing
Devices need to be identified in Ethernet. This is where the MAC-address comes into play. The MAC Address is a 48 bit (so 48 times ones or zeroes) address.
This is an MAC address, in binary format:
- 10111100 10101110 11000101 01100001 11010101 10110101
It can also be represented in hexadecimal format:
- BC-AE-C5-61-D5-B5
Those two are the same address!
Organizational Unit Identifier is a field which is reserved for the creator of the device using MAC -addresses. It takes the first 24 bits of the address. Thus boldened the OUI of the previous address:
- 10111100 10101110 11000101 01100001 11010101 10110101
- BC-AE-C5-61-D5-B5
You can go to Wireshark OUI Lookup Tool to inspect 'BC-AE-C5'
The latter part (61-D5-B5) is the unique device of that manufacturer. This identifies a singular network card e.g.
- Ethernet port on a motherboard
- Mobile phone WLAN chip
- Virtual Machine
Warning: MAC addresses can be faked/spoofed/...
e.g. https://www.digitalcitizen.life/change-mac-address-windows
Also if the same Ethernet segment has two end devices/hosts with same MAC address, problems start to occur. Luckily the chance of this is quite small.
Frame format
Here is an Ethernet Frame.
Ethernet Frames typically are around 1508 bytes long. Unless they are jumboframes, which are 9600 bytes long.
Preample
A 7 byte row of ones and zeroes: 10101010 10101010 10101010 10101010 10101010 10101010 10101010
This byte row aligns the Network Interface Card to make sense of the modulation on the wire.
SFD
The first byte after the preample is 10101011. Notice the last bit.
This informs the the Network Interface Card that a Frame is about to start. The next field will be the destination of a frame.
Destination MAC
Contains the address where the frame is sent.
Unicast address is a singular device (known as a unicast address). The traffic is one-to-one. We earlier had an example of a singular device in the format of:
- BC-AE-C5-61-D5-B5
Broadcast address is meant for the whole Ethernet Segment. The traffic is one-to-all.
A broadcast address is known as all bits 1:
- 1111 1111 1111 1111 1111 1111 1111 1111 1111 1111 1111 1111 (binary format)
- FF-FF-FF-FF-FF-FF (hexadecimal format)
Multicast address is a special address meant for many devices, but not all. So the traffic is one-to-many.
A multicast address has a start of either:
- 01-00-5e-**-**-** for IPv4 multicast
- 33-33-**-**-**-** for IPv6 multicast
Source MAC
The device that sent the frame includes its own MAC -address to the field. This is called a source MAC address. It is used by devices forwarding the frame or receiving it.
EtherType
EtherType gives the receiving or transmitting party the information of what the frame witholds. Most common ethertypes are,
- 0x0800 for IPv4
- 0x0806 for ARP
- 0x86DD for IPv6
All the ethertypes can be found here from IANA
Payload
This contains the payload of the message that was indicated by EtherType. It might be a Layer 2 protocol data (e.g. Spanning-Tree Protocols BPDU) or Layer 3 protocol data (e.g. IPv4/IPv6 Header).
Frame Check Sequence
The Frame Check Sequence is a 32 bit error detecting code to withstand noise from the transmission medium (e.g. electromagnetic interference of radio waves). This noise might alter the bits in the transmission of a frame.
Cyclic Redudancy Check - CRC - value is typically set to this field. Once a frame is received. It can be calculated to notice even small bit errors in the frame. How to calculate a CRC value is out of scope for this course.
Switching
Switching is typically the process of transmitting ethernet frames from one port to another. This means there is a device with a mac address table (aka forwarding table or forwarding information base):
| Port | MAC address |
|---|---|
| 1 | - |
| 2 | - |
By receiving frames the switches learn of MAC addresses around the switches.
Rule: If a frame is received, of which the destination MAC is not known: send it out of all the ports except the one it was received from.
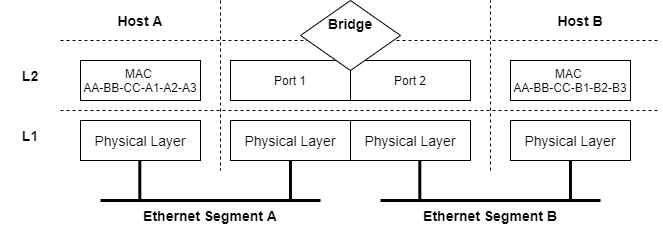
Bridge
These are the basic functionalities of a bridge:
- Learn of devices around them (by MAC addresses)
- Forward frames between ports
- Separate Collision Domains
If both hosts have transmited frames, the mac address table of the bridge would look like this.
| Port | MAC address |
|---|---|
| 1 | AA-BB-CC-A1-A2-A3 |
| 2 | AA-BB-CC-B1-B2-B3 |
Switches
Switch is a multiport bridge. Thus there is e.g. 24 bridges in a switch. These can be seen as todays commercial products in the switches category.
Switches are normally represented by this logo in network topology drawings:
Actual physical switches are discussed later on M05 Devices and Cabling
On Collision Domains
This is something affecting the BUS -topology and means if two frames are sent on the same wire simultaneously. This would mean a spike in amplitude (voltage) of that wire and thus a collision. Two entities are sending at the same time. There are two different collision avoidance principles
- Carrier Sense Multiple Access / Collision Detection (CSMA/CD)
- for Wired networks
- Carrier Sense Multiple Access / Collision Avoidance (CSMA/CA)
- for Wireless networks
These are basic principles of Ethernet networks, but have been laid back in importance as networks have evolved from
- half-duplex to full-duplex in wired networks
- and to multiple input/multiple output (MIMO) in wireless networks
Virtual Local Area Networks - VLANs
Video: Data Networks, Ethernet, Switching and VLANs, part 3
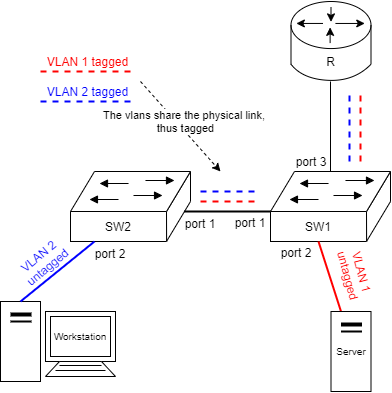
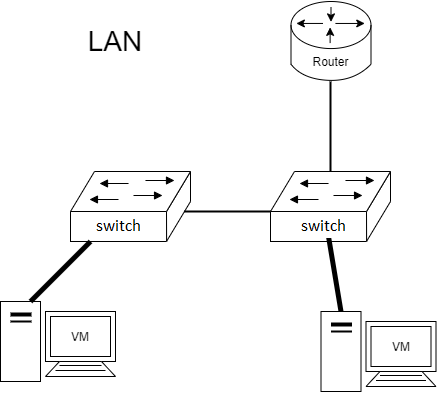
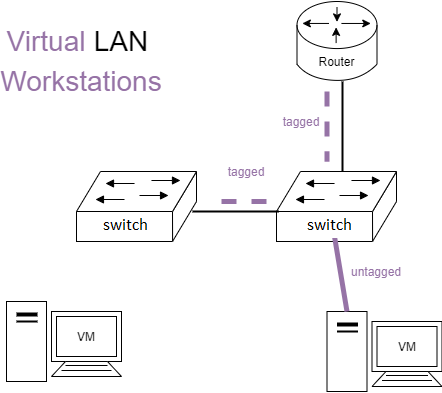
One physical switching infrastructure needs to support multiple separated, logical networks. This is sometimes called network segmentation. The basic use case would be to separate the servers from the workstations. This forces the traffic to go through a gateway device (a router/firewall). See the figure below,
In the figure the ports between the network devices are tagged and the ports to end devices are untagged. Also the devices are separated as follows:
- VLAN 1 - Servers
- VLAN 2 - Workstations
Typically the VLANs have different IPv4 subnets, but we'll come to this later.
802.1Q -standard
Untagged (Ethernet Frames)
An untagged frame means that the Ethernet Frame is as it was earlier defined. The frame is simply without a tag, thus Untagged.
Tagged (Ethernet Frames)
A tagged frame means that an additional ethertype and tag is added into the frame.
The red section (32 bits) goes as follows:
| EthType (16 bits) | Tag (16 bits) |
|---|---|
| 0x8100 | further defined below |
And within it the tag field:
| PCP | DEI | VID |
|---|---|---|
| 000 | 0 | 0000 0000 0000 |
- Priority Code Point - PCP - The Quality of Service of Ethernet Frames
- Drop Eligible Indicator - DEI - in case of congestion, can the frame be dropped (true/false) (earlier it was CFI bit)
- VLAN Identifier - VID - Separates virtual local area networks from one another
- 0x000 - 0xFFF, 2^12
- 0 - 4096 different values
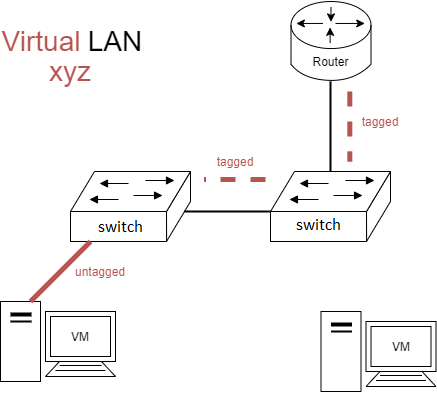
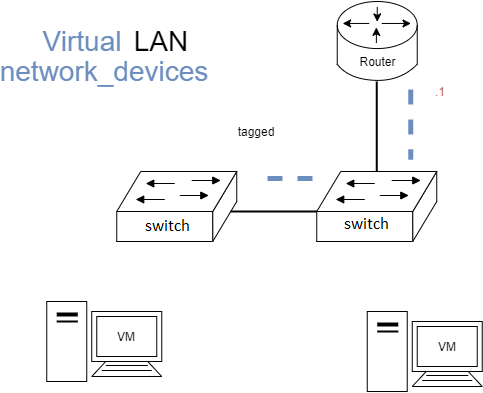
802.1Q Configuration Example
Configuration Example
Given the topology
SW1 configuration
create vlan eppu
conf vlan eppu tag 1
create vlan toppu
conf vlan toppu tag 2
conf vlan eppu add port 1 tagged
conf vlan eppu add port 3 tagged
conf vlan toppu add port 1 tagged
conf vlan toppu add port 3 tagged
conf vlan toppu add port 2 untagged
SW2 configuration
create vlan eppu
conf vlan eppu tag 1
create vlan toppu
conf vlan toppu tag 2
conf vlan eppu add port 1 tagged
conf vlan toppu add port 1 tagged
conf vlan eppu add port 2 untagged
Investigating Traffic
It is illegal to interfere & read communications in Finland!
5 § Vaitiolovelvollisuus ja hyväksikäyttökielto
Se, joka on ottanut vastaan tai muutoin saanut tiedon luottamuksellisesta viestistä tai tunnistamistiedosta, jota ei ole hänelle tarkoitettu, ei saa ilman viestinnän osapuolen suostumusta ilmaista tai käyttää hyväksi viestin sisältöä, tunnistamistietoa tai tietoa viestin olemassaolosta, ellei laissa toisin säädetä.
You can still read data of your own environment (the exercise environment) where you are the sender and/or receiver of communications!
Wireshark
Network analysis can be done via the most popular program for it, called Wireshark.
Wireshark is the world’s foremost and widely-used network protocol analyzer.
Wireshark lets you see what’s happening on your network at a microscopic level and is the de facto (and often de jure) standard across many commercial and non-profit enterprises, government agencies, and educational institutions.
- Deep inspection of hundreds of protocols, with more being added all the time
- Live capture and offline analysis
- Standard three-pane packet browser
- Multi-platform: Runs on Windows, Linux, macOS, Solaris, FreeBSD, NetBSD, and many others
-
The most powerful display filters in the industry
-
Source: wireshark.org
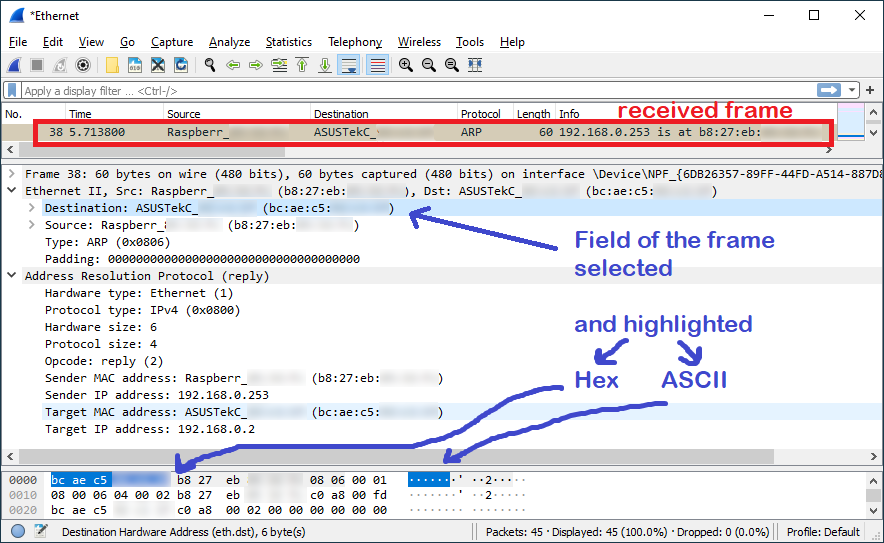
Here is an image of an wireshark capture:
Continue to the Exercises
Self-reflect the material with a small quiz?
![]() Data Networks Quiz - M02 Ethernet, Switching and VLANs
Data Networks Quiz - M02 Ethernet, Switching and VLANs
Back to the Schedule?
License
This course and its materials are written by Karo Saharinen and licenced by Attribution-NonCommercial-NoDerivatives 4.0 International (CC BY-NC-ND 4.0) license.